These Standards Could Protect Your Data From Quantum Computer Attacks
[ad_1]
US govt company on Tuesday named four systems it expects will maintain computer system data mystery when quantum computer systems are mature plenty of to crack modern encryption tech. It truly is a critical action in securing computers towards the possibly revolutionary new technologies.
Researchers confirmed all the way back in 1994 that quantum desktops could split mainstream encryption know-how if the progress in quantum computers could be sustained prolonged adequate. Since 2016, the US Commerce Department’s National Institute of Criteria and Engineering has overseen a hunt to style and design and examination publish-quantum cryptography tech to shield that facts.
Of the four systems that the nationwide institute picked, two are envisioned to be far more broadly utilised.
A single, called Crystals-Kyber, is for setting up electronic keys that two pcs will need to share encrypted details. The other, Crystals-Dilithium, is for signing encrypted info to build who despatched the details. It’ll probable get two a long time for the ways to be standardized plenty of for incorporation into modern program and hardware.
Quantum pcs have been steadily progressing, but it will most likely even now consider a long time of get the job done to make machines that are reputable and powerful plenty of to crack encryption. Regardless, shoring up encryption now is an urgent problem. It usually takes decades to uncover new encryption solutions, make certain they are risk-free and install them broadly. And federal government agencies and hackers can harvest today’s sensitive information and facts with the expectation they are going to be able to crack it later on when the info will nevertheless be valuable.
“We believe 10 to 15 years is a typically held viewpoint on the time scales for attack,” reported Duncan Jones, head of cybersecurity for quantum computer hardware and application maker Quantinuum. “But with the probability of ‘hack now, decrypt afterwards,’ the attacks may perhaps have by now begun.”
Whilst quantum pcs continue being immature nowadays, a host of startups and tech giants like Google, IBM, Microsoft, Amazon and Intel are pouring study dollars into growth and building continuous if incremental progress. Professionals assume quantum pcs to increase the capability of classical machines with new specialist qualities in jobs like acquiring new materials and medicines from the molecular level and optimizing producing.
Normal people most likely need to have not be concerned far too substantially correct now about the menace of quantum pcs later decrypting their information, reported 451 Team analyst James Sanders.
“What’s the value of your sensitive data 1, 5, 10, 20, or far more yrs down the road? For companies or govt, this is additional of a urgent worry, but for every day men and women, issues like credit rating card figures are rotated routinely adequate that this danger isn’t serious adequate to care,” he explained.
Quantum pcs also could undermine cryptocurrencies, which also use modern cryptography technologies.
The National Institute of Requirements and Engineering picked 4 technologies for standardization in component because it desires a varied set for diverse scenarios and for the reason that a broader selection can help defend from any potential weaknesses that are learned. To protect in opposition to some of all those attainable weaknesses, lots of industry experts advise hybrid encryption that employs each typical and write-up-quantum procedures.
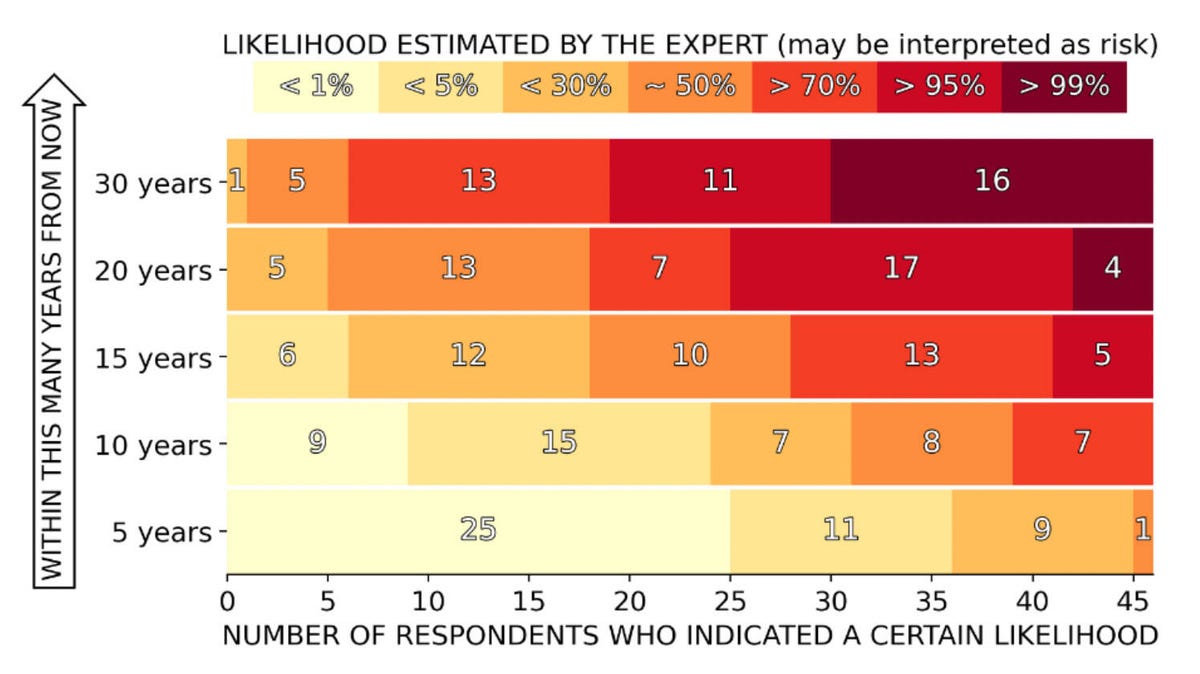
The Worldwide Chance Institute surveyed 47 quantum computing specialists in 2021 about when they imagined quantum computing would come to be a challenge for common RSA 2048 encryption.
World wide Threat Institute
“Ideally, various algorithms will emerge as superior alternatives,” NIST write-up-quantum encryption leader Dustin Moody mentioned in a March presentation. It’s evaluating some other candidates appropriate now.
NIST has been slowly narrowing the listing of write-up-quantum candidates for many years, consolidating some with related strategies and rejecting others with challenges. One particular technology for digital signatures identified as Rainbow created it to the third spherical right before an IBM researcher figured out this year it could be cracked in a “weekend on a notebook.”
Slower efficiency of put up-quantum cryptography
1 hurdle for write-up-quantum cryptography is that it can be not as speedy in some circumstances.
“Quantum-risk-free electronic signatures will incur a a little higher cost,” adds IBM cryptography researcher Vadim Lyubashevsky.
Google sees a slowdown in the vary of 1% to 3%, stated Nelly Porter, a quantum technology specialist at the business. That may perhaps not sound like a lot, but it is for a corporation with as substantially network visitors as Google, which is why it will need hardware acceleration to use submit-quantum encryption. Google has extensively analyzed various article-quantum technologies to check out to highlight troubles like worse conversation latency.
“At our scale you would not be able to transform it on by default for every thing,” Porter reported.
NXP is developing an accelerator chip to pace issues up working with the systems that NIST has begun standardizing and expects to ship them when the criteria them selves are concluded by 2024. Hardware acceleration will be needed in individual for gadgets with constrained processing electrical power and memory, claimed Joppe Bos, NXP’s senior principal cryptographer.
Embracing submit-quantum encryption
Although NIST is only now naming its first expectations, numerous corporations by now have begun creating, applying and offering write-up-quantum encryption in goods:
IBM’s newest z16 mainframes support both of those Crystals-Kyber and Crystals-Dilithium, systems IBM by itself assisted build.
Google has analyzed a number of write-up-quantum encryption systems and expects to adopt them to shield interior and exterior network website traffic. Its exams disclosed some incompatibilities that organization companions have resolved, it reported Wednesday.
The NATO Cyber Stability Centre has started screening put up-quantum encryption technological innovation from a British firm termed, fittingly, Post-Quantum.
Amazon Net Companies, an enormously broadly employed basis for many other companies’ computing needs, delivers Kyber encryption technology assistance.
Infineon offers a chip made use of to guard devices from firmware updates otherwise susceptible to quantum pcs that could sneak malware on to equipment.
[ad_2]
Resource website link







